First, I want to say that I am a big supporter of Grooveshark. I think it’s an awesome service and I have purchased merch from them. That being said, yesterday I started looking for a way to rip the songs from Grooveshark. It has been a while since I kept an up-to-date music collection.
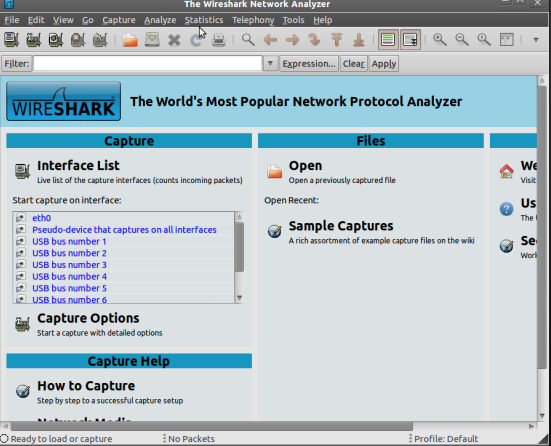
The files that are streamed to your computer are temporarily stored on your local machine. This means that we can save the packets that are being sent to your computer as an actual audio file. First, we need to use a network protocol analyzer that will allow us to find the packets being sent the to the computer. This is where Wireshark comes in. We can start by downloading Wireshark and installing it. (not going to show you that here) Once we have it running, it should look like this: (May need to run as root)
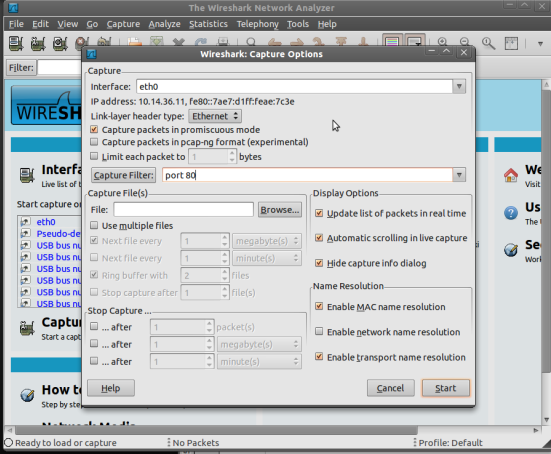
Next we need to configure some settings. Since we know that we are accessing Grooveshark through a web page is a good bet that they are pushing these packets over http. We will limit the filter to only capture port 80 traffic since that’s all we really care about right now. Set this up in Capture -> Options. See below.
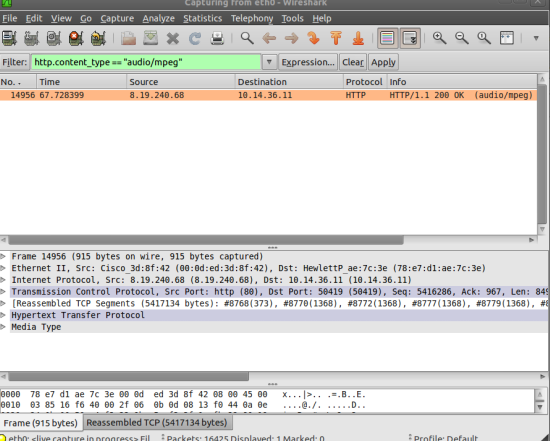
Now we can start the capture. Next go the the Grooveshark site and start playing a song. There will be a lot of packets showing up in your list. The main packet that you are looking for is one with a type of “audio/mpeg”. You can also make this easier if you use this filter: http.content_type == “audio/mpeg”
If you use the filter method then you should only see one packet show up. It should look something like this:
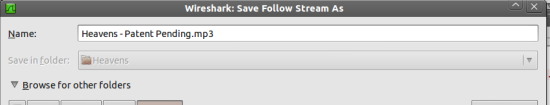
Right click on the packet and choose follow tcp stream. This should assemble all the related packets and bring up a summary asking you what you would like to do with the packets. On the right hand side there will be some options for how you would like to save your stream content. Choose “Raw” and click the “Save As” button. You can now save the file as whateveryouwant.mp3. You can now go to the folder that you saved it in and play the file in your favorite music player. (May need to chmod the file if was downloaded by root.)
Note: I found someone who has done the same thing when I was looking how to save the stream. So I can not take 100% credit for this.
Also: I looked into writing something to automate this process but there is already another project that is doing this. Check out http://groovedown.tasteless.us/